It's a nail biter. Eleven teams of hackers from around the globe meet in Miami for what some say is the biggest industrial hacking contest in the world. Who will take the big prize in Pwn2Own Miami 2022?
Read MoreHuman or hoax? Here are three ways to check if a video is real or a deepfake, an artificial person created by computers.
Read MoreHackers invaded computer systems of one of the biggest energy companies in Ukraine and tried to cut power for a large number of people, Ukraine’s government said in a press conference. A response team stopped the attack, but not before damage was done, they reported.
Read MoreCan cyber attackers crash a train? Here’s what attackers are most likely to do to trains with passengers in 2022 and how people can try to stop them.
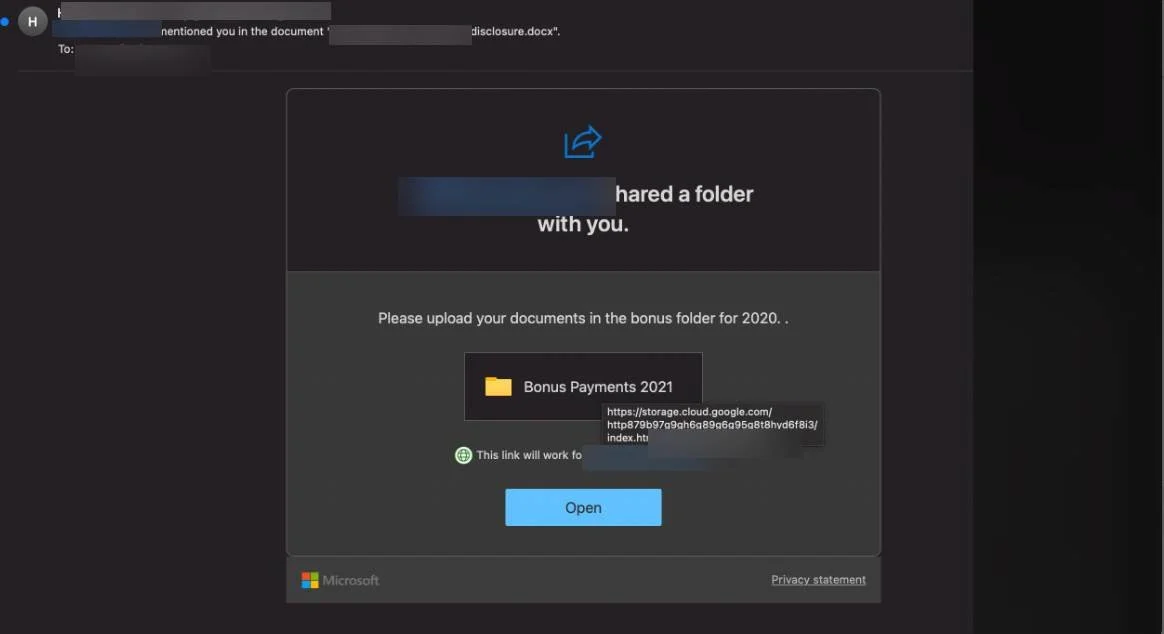
Read MoreAs the battle continues in Ukraine, attackers are sending out poisoned emails to trick people out of their passwords. See what the emails look like and how to protect yourself against these and other attacks coming in to your inbox.
Read MoreHow can you prepare for cyber war after the Ukraine invasion? Experts say you can take a simple step to keep attackers away from your computer.
Read MoreYou might think you’re protected if someone steals money from your retirement account. But that may not be true. Victims of a $36 million retirement account theft are wondering if they will get their life savings back. The law, however, may not be on their side.
Read MoreWhen it comes to passwords, people love animals, superheroes and toilet humor. See which popular words and phrases made the top 10 list of the world's most entertaining yet extremely hackable passwords.
Read MoreWho is number one in cyber crime and cybersecurity this year? We show you how countries ranked in crimes like spam, ransomware, cryptomining and more.
Read MoreWatch out for deepfakes in your LinkedIn connections. Someone is posting fake profiles with fake pictures and you may be their target. We investigate a deepfake case racking up 100’s of connections with potentially sensitive accounts, plus what could happen if you accept the connection request.
Read More