The attack is coming from inside the printer! A researcher shows how cyber crooks can pose as your printer to attack you and steal your stuff as well as what you can do to stop them. Two small steps can make a big difference and protect your from cyberattacks.
Read MoreWhat is the encabulator? It's a fake machine, a joke that's lived on for nearly 80 years. It became famous as the retro encabulator and the turbo encabulator. Now, there is a new chapter in encabulator history: the hyper encabulator.
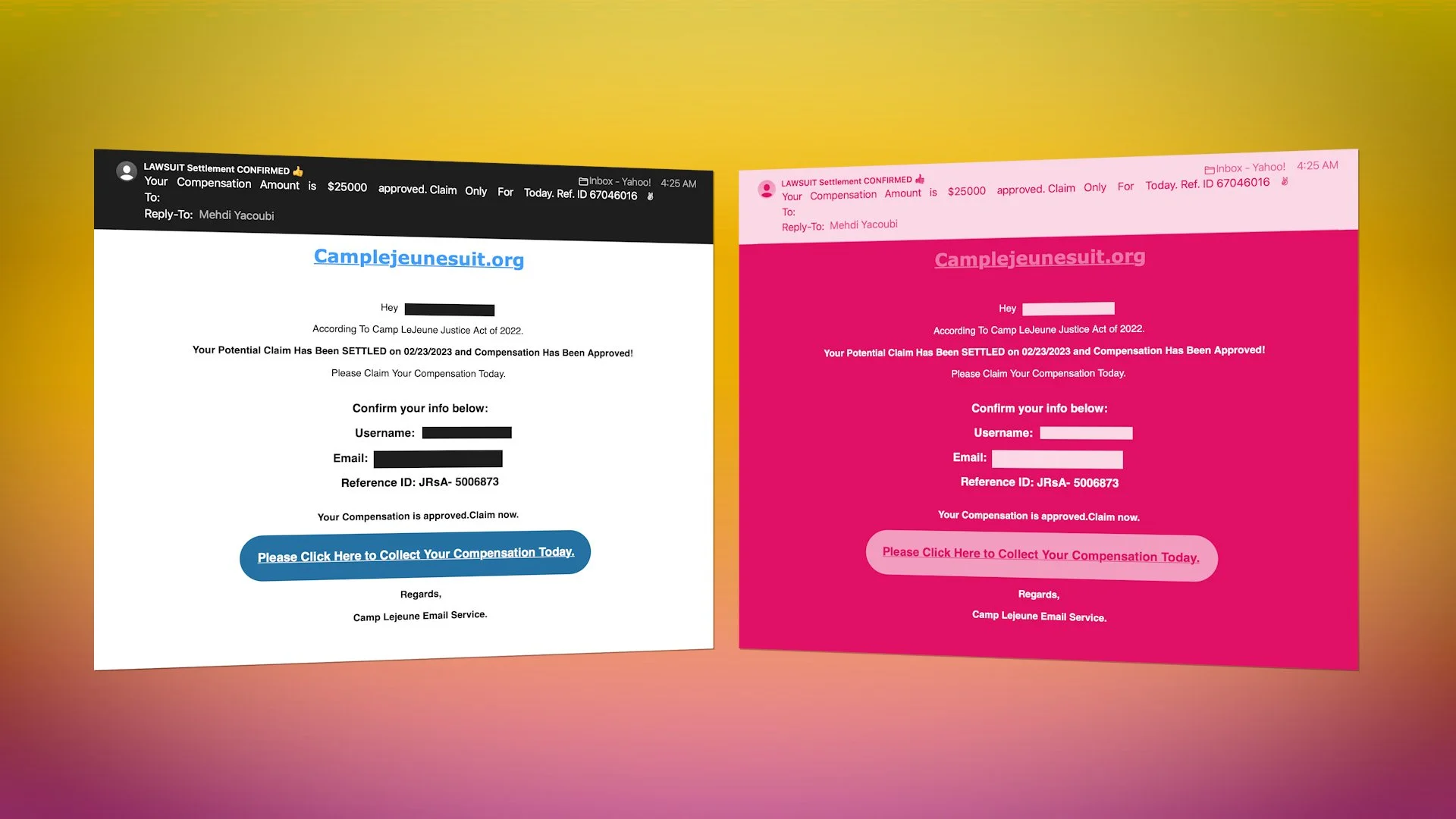
Read MoreCyber crooks are trying a clever tactic. They're sending you one email with two different looks, one for your phone and one for your laptop. This phishing strategy might just convince you to click on their scam links. Here's what to look for.
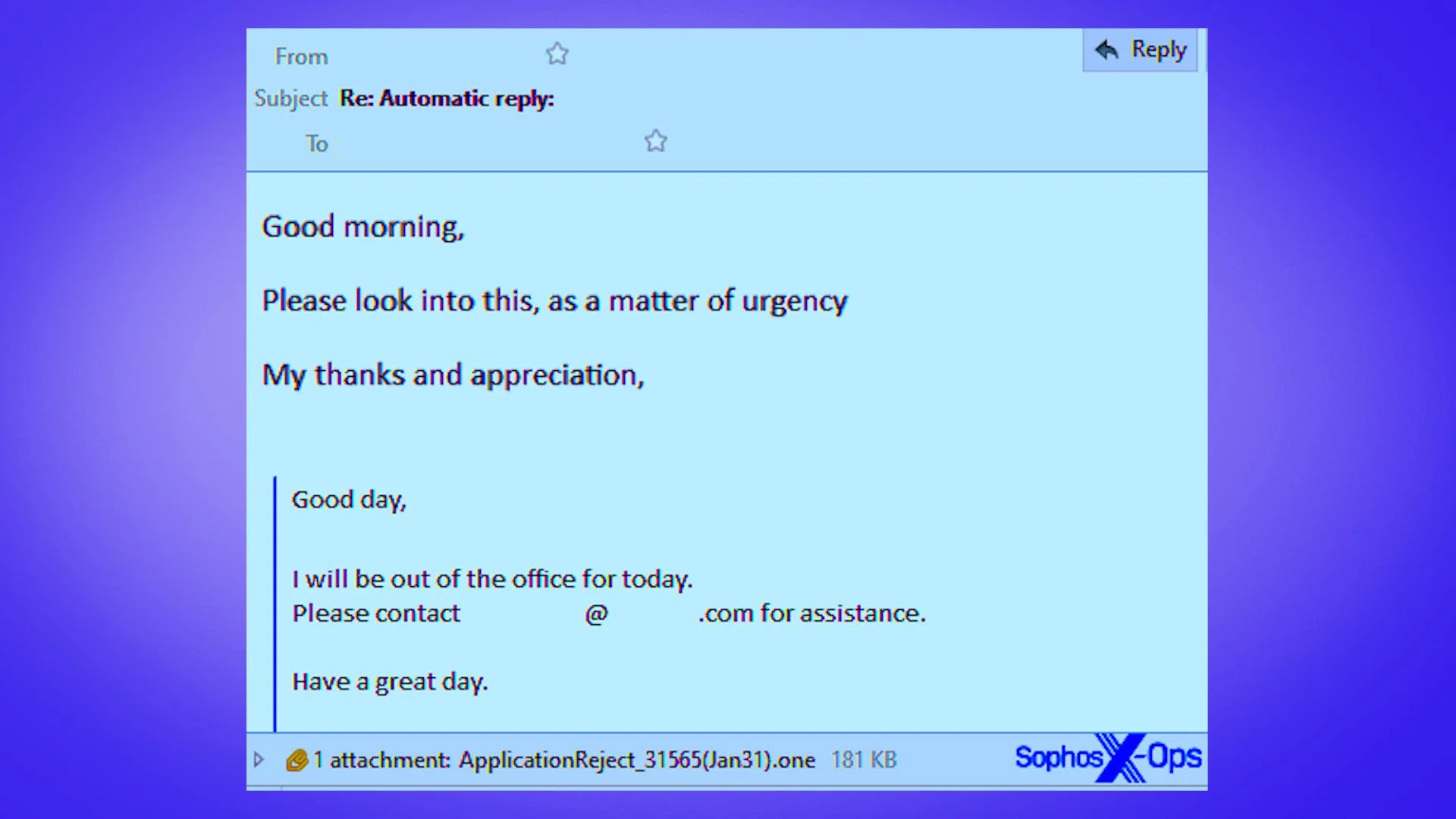
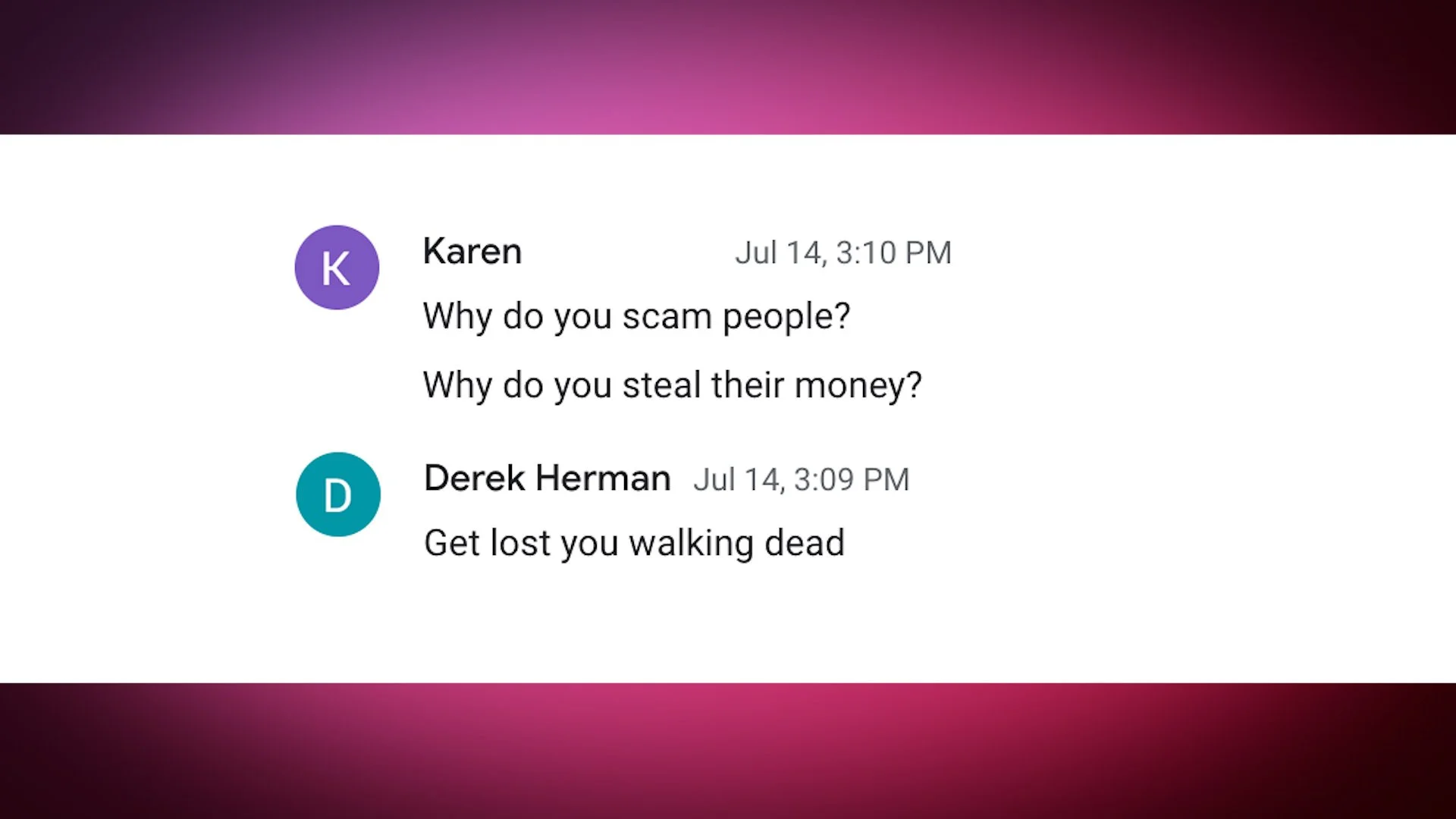
Read MoreYou already know to watch for fake emails from attackers. But here's a bit of a twist. Cyber crooks are jumping into your email conversations to send you their own poisonous replies, and they're using fresh tactics along the way. Here's what to watch for and how to avoid the cyber crook 'reply guys' who want to take your money and passwords in thread hijacking attacks.
Read MoreOne year after the launch of the Russian war against Ukraine, we interview a Ukrainian cyber defender who spends her days and nights protecting data and infrastructure from cyberattacks. Her attitude and her views may be surprising to people outside of this country ravaged by war.
Read MoreWant to know how to make a catfisher sing? We take you inside a romance scam investigation to show you the crooks’ current tactics, plus you’ll hear some choice songs from the scammer.
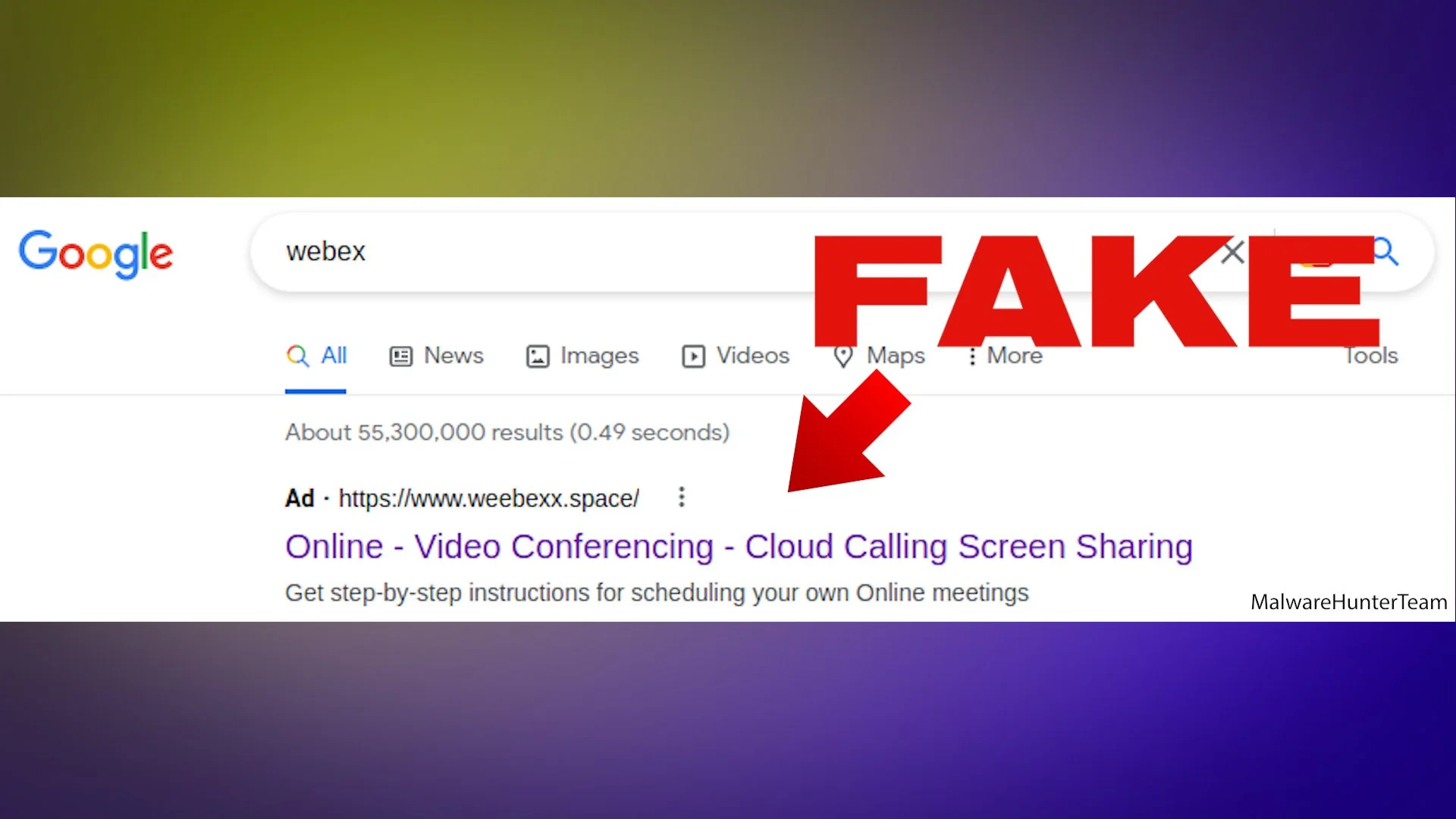
Read MoreDoing a search online? Watch out for fake Google ads promoting criminal sites that can steal your money and passwords. Here's how to detect the fakes.
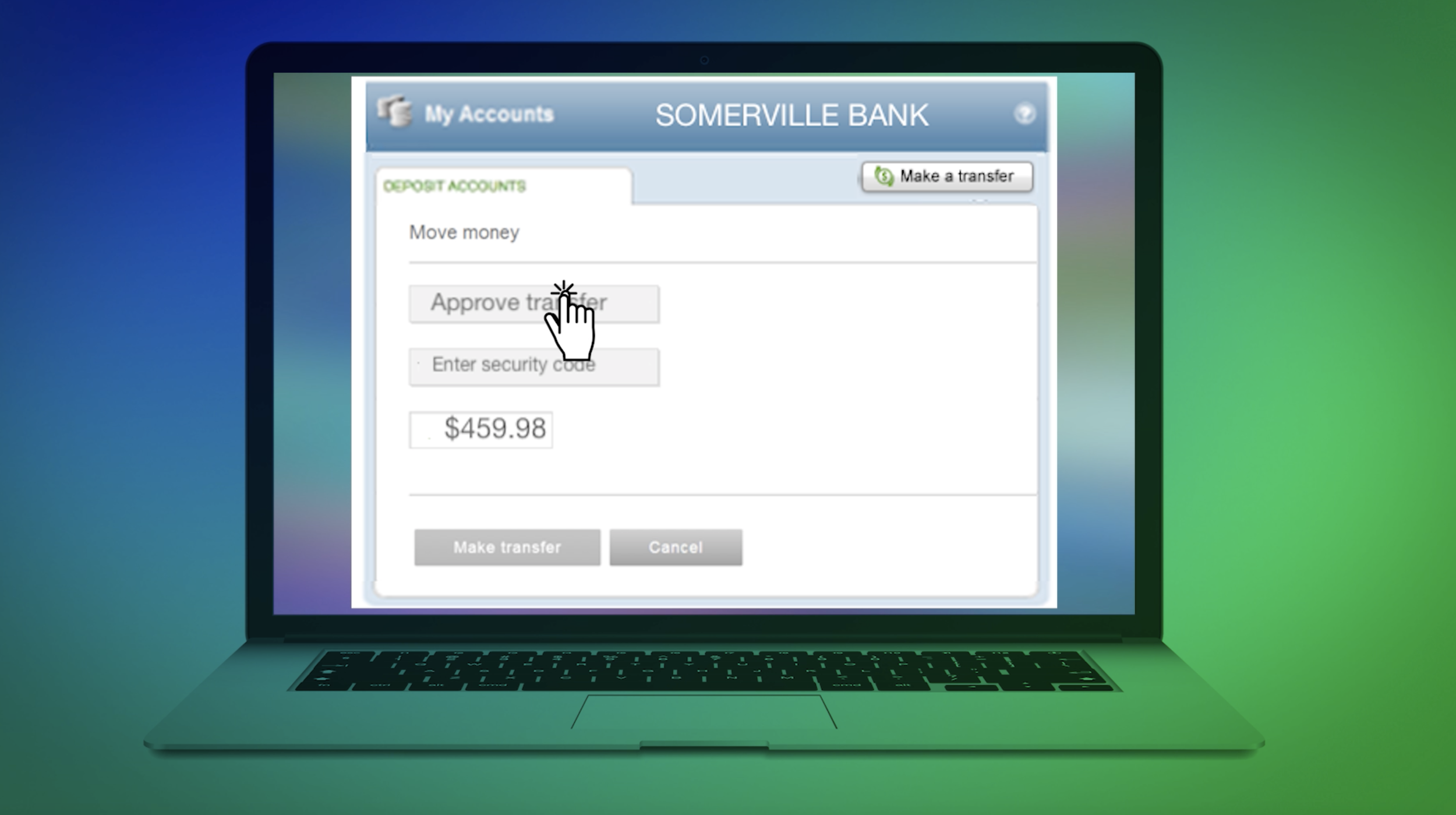
Read MoreYou think you're getting a refund. But in this scheme, cyber crooks are locking up your screen, messing with your bank account, and making off with your money --- all right in front of you. Here's how it works and how to protect yourself in this latest episode of Cyber Tricks Revealed.
Read MoreAttackers are targeting the machines that run our world, like power, gas and water. This year they created two new pieces of industrial malware, bringing the world total to 7.
Read MoreAre you oversharing? Giving away too much about yourself on social media? Here are three questions to ask yourself about your posts from a social engineering expert.
Read More