Understanding NERC's CIP-004-7 and CIP-011-3: A Deep Dive into BCSI Access, Cloud Challenges, and Encryption
By jason smith
Get prepared with a comprehensive overview of NERC's new Critical Infrastructure Protection (CIP) standards, CIP-004-7 and CIP-011-3, set to be effective from January 1st, 2024. Understand the pivotal changes concerning BES Cyber System Information (BCSI) access, the nuances of cloud BCSI, and the strategic choices around encryption.
Effective January 1st, 2024, North American Energy Reliability Corporation (NERC) registered entities were required to comply with two new Critical Infrastructure Protection (CIP) standards:
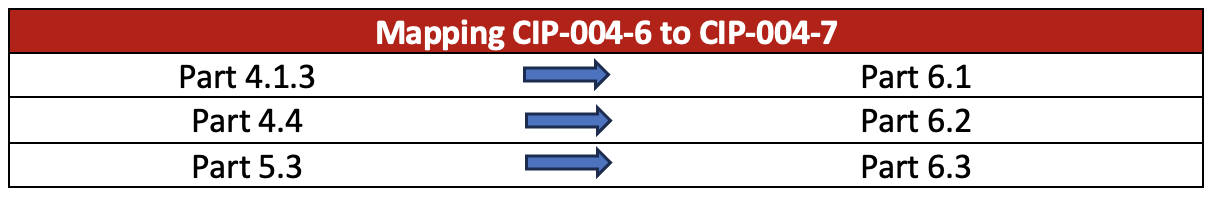
Changes to both standards primarily address revisions to BES Cyber System Information (BCSI) and allowances for cloud BCSI. As a result, language in both of standards was updated and CIP-004 sub requirements were restructured as follows:
CIP 004 7 moved authorization for BCSI access from Requirement R4 to a new Requirement, R6
R6 explains what is meant by the term “Access” and introduces a new term, “Provisioned Access”
CIP 011 3 Requirement R1 has been simplified to provide greater clarity and flexibility in implementing information protection
CIP-004-6 to CIP-004-7 sub requirements restructuring
New CIP-004-7 Terms Defined
What is “Access” to BCSI?
It is defined as both the ability to obtain and use BCSI
What is “Provisioned Access”?
The result of the specific actions taken to provide an individual the means to access BCSI
May include physical keys or access cards, user accounts and associated rights and privileges, and encryption keys
Types of Access Authorization
BES Cyber Systems (BCS), Electronic Access Control and Monitoring Systems (EACMS), and Physical Access Control Systems (PACS) typically contain BCSI. Access to this form of BCSI is authorized through your current CIP-004 R4 electronic and physical access management programs. They do not require a separate BCSI authorization
Access to BCSI documentation that resides in document repositories, workflow management systems, cloud based storage, etc. should be authorized through a BCSI access management process and documented as such.
Keys to Successful CIP-011-3 Information Protection Programs
Programs will be required to prevent the compromise of BCSI confidentiality and prevent unauthorized access to BCSI. BCSI locally on-premise can leverage existing electronic and physical security controls within current CIP programs. However, the CIP-011 version 3 allows for entities to leverage BCSI in the cloud. The benefits of BCSI cloud solutions will also present challenges requiring mitigating controls to ensure cloud provider do not have the ability to obtain and access use BCSI or require integrating personnel that may have that ability into CIP-004 access management programs.
Access management program integration of cloud providers though compliant presents challenges that have plagued the industry historically. Challenges such as removing access to BCSI by the next calendar day in the event of a personnel change. Further the reliance that the cloud provider will inform the entity of personnel changes in a timely manner to ensure access is removed within the mandated timeframes. Additionally there is the risk that new cloud provider personnel having the ability to obtain and use BCSI without properly notifying the entity and obtaining the proper authorization in advance.
Encryption will be a standard protection utilized for cloud BCSI. Encryption will require implementing one of two Encryption Key Management Program models.
Model 1: Entity-managed Encryption
In this model the entity manages the encryption keys in a Hardware Security Module (HSM), on their own premises, via a 3rd party separate from the cloud service provider, or in a service within the cloud solution. HSMs perform key management and encryption operations. An HSM that resides on the entity’s network (on prem, with a 3rd party, or in the cloud) can offer high speed encryption of your information and inhibits the cloud provider from having access to the keys and thus the ability to decrypt and use BCSI.
This approach is both simple and secure, however the disadvantage is that the cloud provider may not be capable of providing support to the entity if encryption keys are lost. It requires special attention by the entity to properly manage encryption keys locally or via a third party solution.
Model 2: Mutually-managed Encryption
In this model the cloud provider has some or all control of the encryption process. The entity and provider share access and management of the encryption keys. As a result the provider will likely have the ability to access BCSI. The advantage is the ability of the provider to support additional services and lost key mitigation. The key disadvantage is the cloud providers access introduces BCSI disclosure risk to unauthorized personnel and mandates incorporating the provider into the CIP access management program.
Conclusion
Each entity will need to carefully assess which path to choose. Weighing the advantage of each approach versus the risk introduced by the disadvantages of each model. Every environment is different; thus risk tolerances vary from organization to organization.
Compliance policies, plans, and procedures will need to be updated on or prior to the mandatory compliance date on January 1st, 2024. Documentation will need to capture the approaches you choose to implement, the newly defined terms, and detailed access and controls tracking to ensure ongoing compliance.