Shopping too quickly can cost you! Some companies are adding in surprises at checkout that could leave you paying for something you did not want or expect. Here's one sneaky way they're doing it.
Read MoreFake voice attacks are coming in through your phone and your social media. A new round of Elon Musk fakes shows how criminals are using the clones against you and how you can detect them. In this latest scam ad on YouTube, the Elon clone claims you're one of 45 people he's hand-picked to try out his new money-making venture.
Read MoreCyber attackers from the Russian military hacking group Sandworm used a new technique to shut off electricity in a city in Ukraine on October 10, 2022, according to a new report by security company Mandiant, now owned by Google.
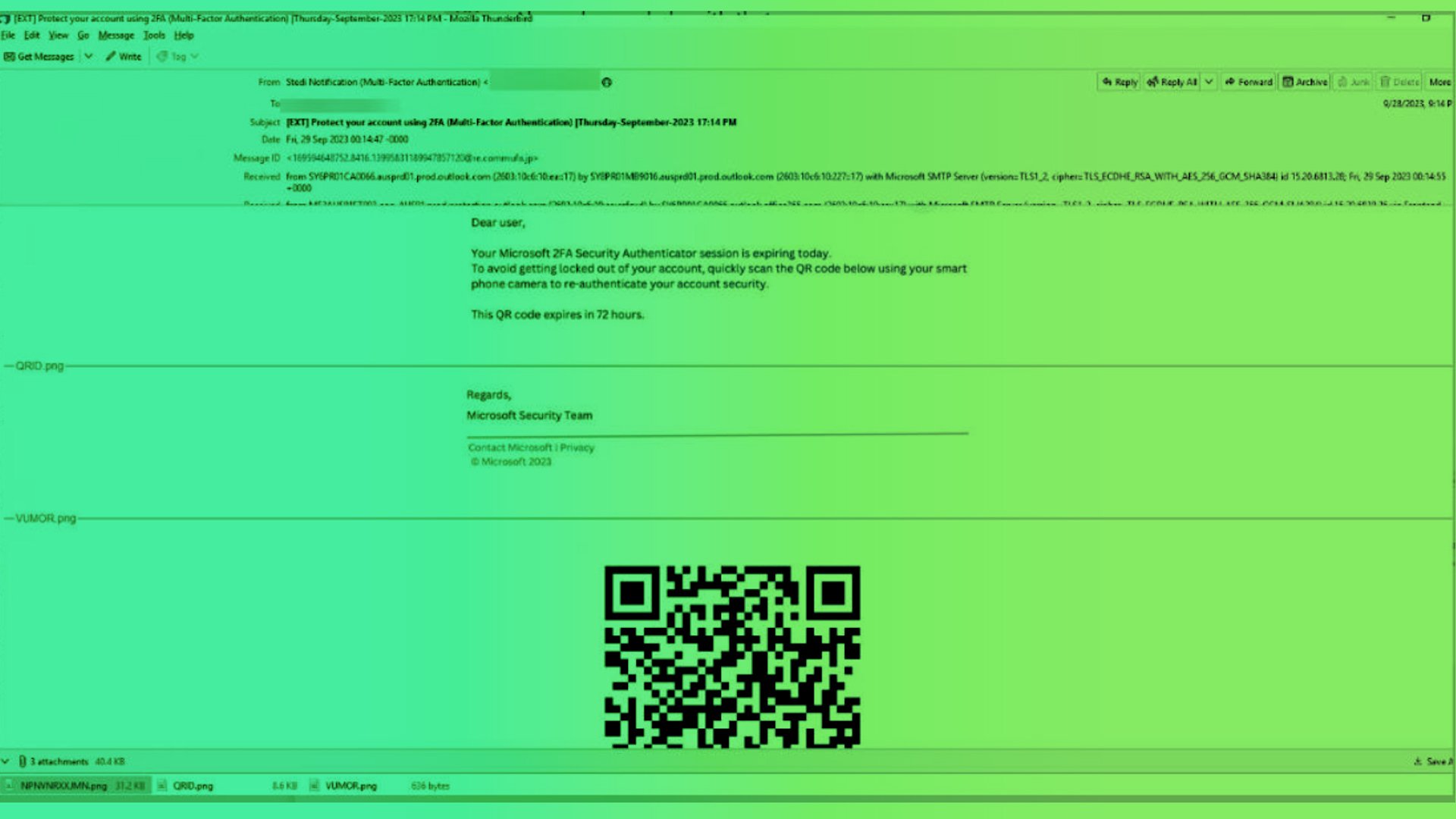
Read MoreYou may use QR codes to look at menus in restaurants. Cyber crooks want to turn that habit into a jackpot. They’re sending out waves of attack emails with QR codes in them, hoping you’ll scan without thinking. Then they’ll try to grab your passwords, data, and money.
Read MoreYou're usually safe to swim in the waters of an official app store. But from time to time, predators find their way in. Here's how to avoid the latest attack apps that can infest your phone with digital sharks.
Read MorePeru gets more than its share of phishing emails. Here are three scam tactics uncovered in fake emails seen in Peru and three ways to protect yourself from these cyber scams.
Read MoreThe future is here. Attackers have begun to use artificial intelligence to write effective and realistic phishing emails, just as security experts predicted. The target here: people at six universities. Now we need to change how we look at suspicious emails to protect ourselves even further.
Read MoreScammers have found an easy way to trick us by sending real PayPal invoices from a real PayPal email address. It's easy for them to do and it can fool you into paying or, even worse, calling to stop the purchase. Here's how it works.
Read MoreThieves are raiding your rewards accounts, looking for air miles and hotel points to steal. They're turning your rewards into their riches, running illegal travel agencies on the underground market. Here's how they get into your accounts and how to stop them.
Read MoreThe attacks come from above, and from the inside, as digital snipers scan Ukraine's energy system for a way in. Here's how Ukraine's energy workers are trying to keep cyber attackers out, all the while dodging missiles and mines.
Read More